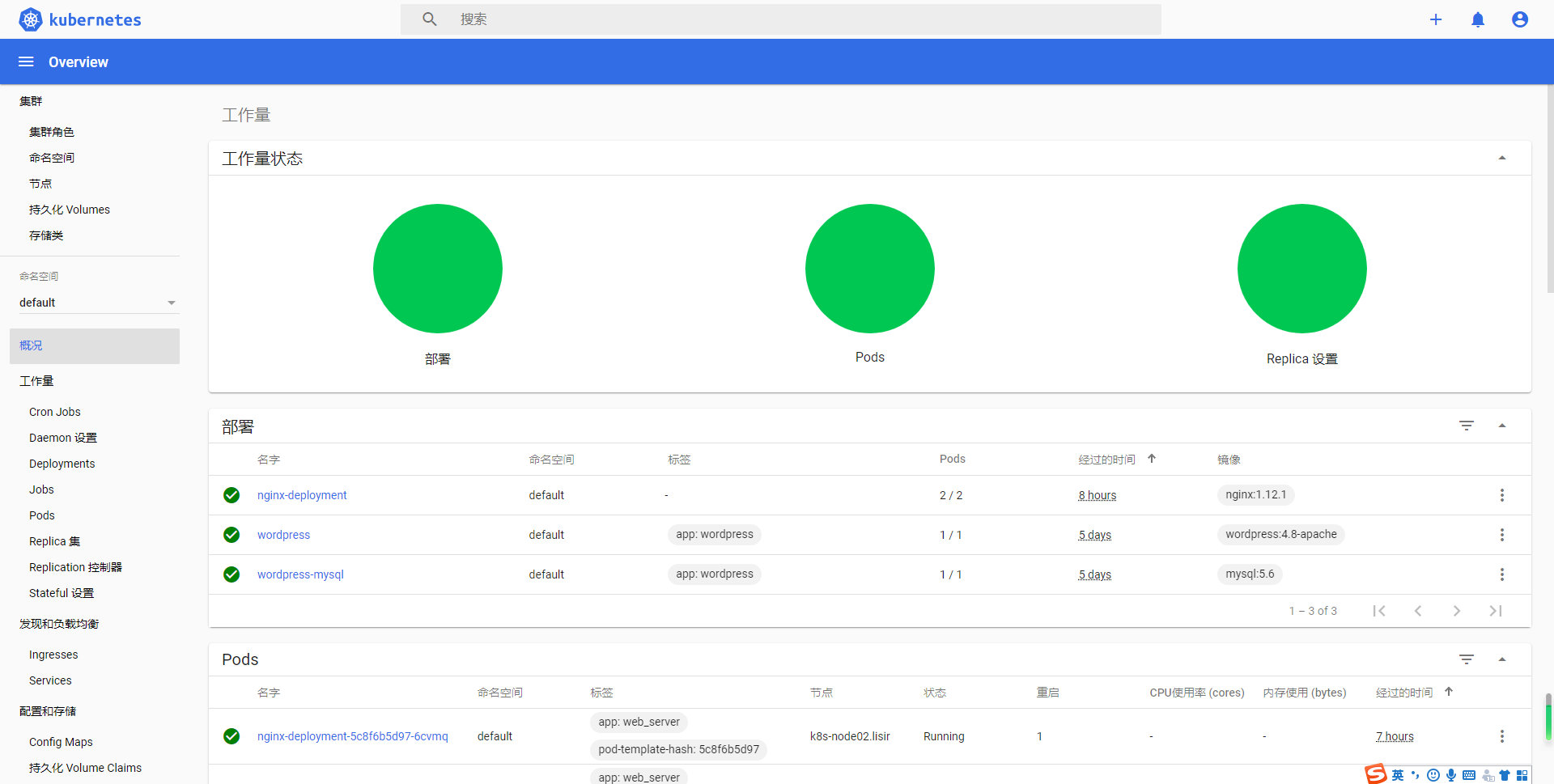
解决k8s dashboard 部分浏览器无法访问的问题
1、查看证书资源
1 | [root@k8s-master http_ssl]# kubectl get secrets -n kubernetes-dashboard |
2、生成自签证书
2.1、openssl生成ca根证书,生成root-ca的key
1 | openssl genrsa -out "root-ca.key" 4096 |
2.2、通过ca的key生成csr文件
1 | openssl req -new -key "root-ca.key" -out "root-ca.csr" -sha256 -subj "/C=CN/ST=SC/L=CD/O=lisirGroup/CN=lisirRootCA" |
2.2、配置ca证书
1 | cat > root-ca.cnf << EOF |
2.3、签发根证书
1 | openssl x509 -req -days 3650 -in "root-ca.csr" -signkey "root-ca.key" -sha256 -out "root-ca.crt" -extfile "root-ca.cnf" -extensions root_ca |
3、ca根证书颁发server端证书
3.1、生成站点 SSL 私钥
1 | openssl genrsa -out "dashboard.lisirk8s.com.key" 4096 |
3.2、使用私钥生成证书请求文件
1 | openssl req -new -key "dashboard.lisirk8s.com.key" -out "dashboard.lisirk8s.com.csr" -sha256 -subj "/C=CN/ST=SC/L=CD/O=lisirGroup/CN=dashboard.lisirk8s.com" |
3.3、配置证书,新建 site.cnf 文件
1 | cat > site.cnf << EOF |
注意:上面的DNS和IP为选填部分,需要填写为server端的域名或ip
3.4、签署站点 SSL 证书
1 | openssl x509 -req -days 750 -in "dashboard.lisirk8s.com.csr" -sha256 -CA "root-ca.crt" -CAkey "root-ca.key" -CAcreateserial -out "dashboard.lisirk8s.com.crt" -extfile "site.cnf" -extensions server |
4、替换https证书
4.1、删除原来的证书
1 | kubectl delete secret kubernetes-dashboard-certs -n kubernetes-dashboard |
4.2、生成新的证书
1 | kubectl create secret generic kubernetes-dashboard-certs -n kubernetes-dashboard --from-file=dashboard.crt=./dashboard.lisirk8s.com.crt --from-file=dashboard.key=./dashboard.lisirk8s.com.key |
4.3、删除原kubernetes-dashboard,让其自动重启加载新的证书
1 | kubectl delete pod kubernetes-dashboard-7d8466d688-7zq6z -n kubernetes-dashboard |
5、查看dashboard-admin用户token
1 | kubectl describe secrets -n kube-system $(kubectl -n kube-system get secret | awk '/dashboard-admin/{print $1}') |
6、导入ca证书到信任的根证书机构
从操作的服务器上将root-ca.crt下载下来,导入到需要访问的电脑中,并添加到受信任的颁发机构
7、各大浏览器进行测试